Describe four key ethical and moral dilemmas that are brought about by implementation of MIS in organizations, illustrating with examples from real life. Describe how you would deal with each of these dilemmas as a manager.

Describe how you would deal with each of these dilemmas as a manager.
Information Systems and Ethics
Information technologies and especially the internet bring about immense social changes, posing possible threats to already existing societal rules, privacy and ethics. Technological trends introduce new situations and questions that managers have never dealt with before. They also raise new kinds of crimes, like cyber-crimes.
A lot of personal information about us is readily and easily available. There are massive databases maintained by commercial companies and Government agencies that allow profiling of personal information. It might take a while before socially acceptable policies and practices are in place given the dynamic and explosive nature of issues raised by Management Information Systems
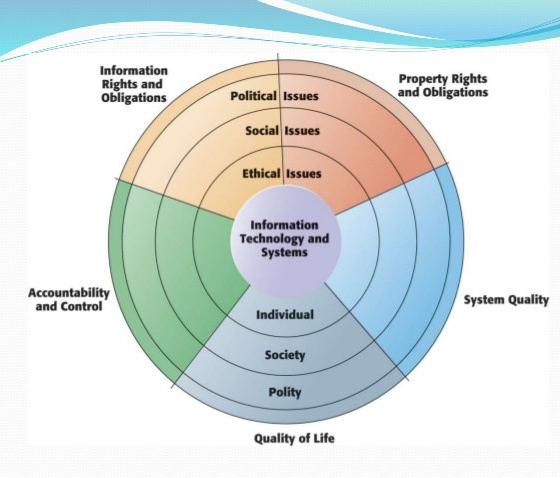
Key Ethical and Moral Dilemmas brought about by Implementation of MIS in Organizations
Source: http://paginas.fe.up.pt/~acbrito/laudon/ch5/chpt5-3main.htm
1. Information Rights and Obligations: Privacy and Freedom
When it comes to information rights and freedom, we need to ask ourselves several questions: What information rights do individuals and organizations possess with respect to information about themselves? What can they protect? What obligations do individuals and organizations have concerning this information?
Privacy is the claim of individuals to be left alone, free from surveillance or interference from other individuals or organizations, including the Government. Information technology and systems threaten individual claims to privacy by making the invasion of privacy cheap, profitable, and effective through the use of web cookies, web bugs, Google user profiling and scanning tools and managed databases with Personal Information. Claims to privacy are also involved at the workplace: Millions of employees are subject to electronic and other forms of high-tech surveillance (Ball, 2001).
Real Life Example: After subscribing for the Safaricom Fibre to Home Internet package and paying via M-Pesa, I got a call from a market survey firm that was conducting research on the quality of service form Home Internet Service Providers – was this just by coincidence?
More Examples here: http://www.nairobibusinessmonthly.com/consumer-privacy-and-data-protection-in-e-commerce-in-kenya/
Dealing with Information rights and obligations:
– Facilitate inclusion and training of employees on terms and conditions for systems in use
– Use of The Platform for Privacy Preferences (P3P) to automatically communicate a user’s preference privacy policy to Web sites such as e-commerce sites
2. Property Rights: Intellectual Property
Here we ask ourselves: How will traditional intellectual property rights be protected in a digital society in which tracing and accounting for ownership is difficult and ignoring such property rights is so easy?
Information systems continue to challenge existing law and social practices that protect private intellectual property. Intellectual property is considered to be intangible property created by individuals or corporations. Information technology has made it difficult to protect intellectual property because computerized information can be so easily copied or distributed on networks.
Real Life Example: Most IT firms have software developers who create systems for them – the question would be: who is the owner of the source code? We would argue that the IT firms owns it because they have employed the individual, but isn’t the software developer the creater and therefore the owner of the system?
Dealing with Property Rights:
– For managers, it is important to communicate the companies Intellectual property policies of a company with a potential employee.
– For most innovators and developers in Kenya, they can register their intellectual property in the new copyright registration system dubbed IP Hub can be of great assistance in copyright
Read more here: http://www.businessdailyafrica.com/magazines/Kenyans-face-hurdles-search-intellectual-property-rights/1248928-3823878-q40396/index.html
3. Accountability, Control and System Quality
Who can and will be held accountable and liable for the harm done to individuals, collective information, and property rights?
As Technology advances and networks such as the internet become more complex, who is to be held accountable for illegal dealings, underground websites or pornography? Some argue that Internet Service Providers must be held accountable but the question is, how much control do they have over what is transferred through their networks? It is becoming more challenging even with simple issues such as system failures and who needs to be held accountable. Should it be the system supplier or the infrastructure in place? And who should pay for any inconveniences experienced
Real Life Example: On April 24 this year, Safaricom Network suffered service outage between 9:40am and 4:30pm in a disruption that paralyzed a lot of businesses and transactions. Some organizations were unable to pay wages, pay their bills on time and customers were gravely affected leading to a ripple effect even on the economy. Was Safaricom solely to blame for this? Should we hold them accountable for the harm caused in the economy? Shouldn’t the government
Read more here: http://www.nation.co.ke/news/Safaricom-network-breakdown-affects-millions/1056-3901410-ixo1sqz/index.html
Dealing with Accountability and Control
– As managers we need to have backup and redundancy measures for such incidents
– Even in organizations, it is important to have Proxy servers that block websites that contain indiscreet content
4. Quality of Life: Equity, Access, and Boundaries
What values should be preserved in an information- and knowledge-based society? What institutions should we protect from violation? What cultural values and practices are supported by the new information technology?
The negative social costs of introducing information technologies and systems are beginning to mount along with the power of the technology and ease of access of the technology.
One of the main social and ethical changes in the work environment is maintaining boundaries and working within the eight-hour a day schedule. In some organizations, you find that emails and calls are still made after work hours. The work umbrella now extends far beyond the eight-hour day leaving less time for family and other life concerns
Read https://www.fastcompany.com/3061960/what-sending-after-hours-emails-does-to-your-productivity
Disposal of technological gadgets that become obsolete is also a major challenge environment conservation
Ergonomics: poorly designed or improperly adjusted computer desks in the workplace can result to unnecessary fatigue, stress, and even injury.
portable for nearly a century), the advent of information systems, coupled with the growth of knowledge-work occupations, means that more and more people will be working when traditionally they would have been playing or communicating with family and friends.
Dealing with Quality of Life:
– Create formal that can mitigate the negative effects of an always-on culture. You can instill a strict ban on after-hours emails, or state that emails after hours don’t have to be returned until work hours the next day.
– Office Desk designs that take into account computer ergonomics